Cybersecurity Maturity Model Certification (CMMC)
The Cybersecurity Maturity Model Certification (CMMC) is being revised and when adopted, will be very different from the original model. Furthermore, the adoption of Model 2.0 is going to be substantially delayed pending normal government processes. Last night (November 9, 2021), it was disclosed that the review process will take between 9 and 24 months with a mandatory 60-day public comment period thereafter. In other words, the earliest effective date for Model 2.0 is October 2022. It is important to understand that no individual or organization can move you towards CMMC Model 2.0 certification at this time as the new requirements are not finalized.
It was also disclosed that the original number of organizations requiring certification was approximately 300,000 and under the proposed model, that number drops to approximately 12,000, with many expected to be able to self-certify.
The delays, proposed changes, and implementation timeline should not be construed as a reason to stop paying attention to your cyber security posture. Instead, take this additional time to review your existing cyber security program and implement necessary changes ahead of the eventual adoption of CMMC Model 2.0.
The graphic below highlights the basic differences between the original model and Model 2.0.
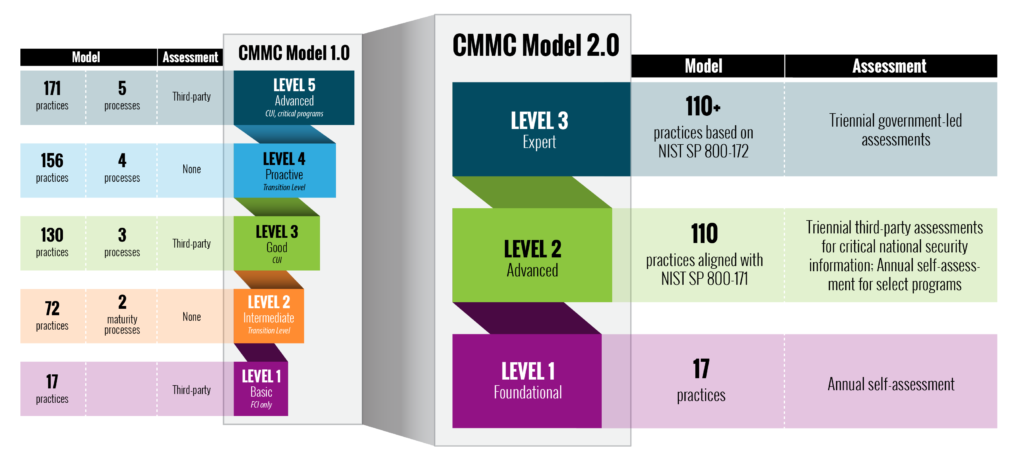 Source: dodcio.defense.gov/CMMC/
Source: dodcio.defense.gov/CMMC/
CMMC certification requirements continue to be a moving target and the most current CMMC information can be found on the U.S. Department of Defense website by following the links below.
The main page for CMMC Model 2.0 information can be found here.
JANUS will be one of the approved organizations to help you achieve CMMC Model 2.0 certification when the program is finalized, and certification is possible. We can help you protect your operations and infrastructure now while preparing for the future.
To find out more about FAQs involving the CMMC model, click here.
